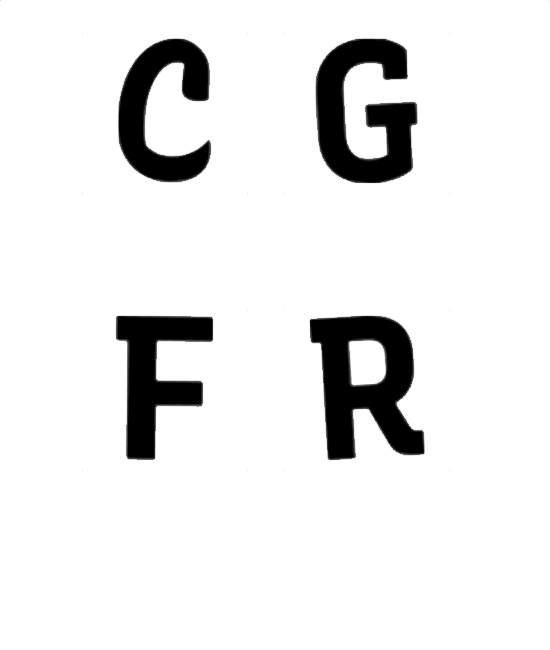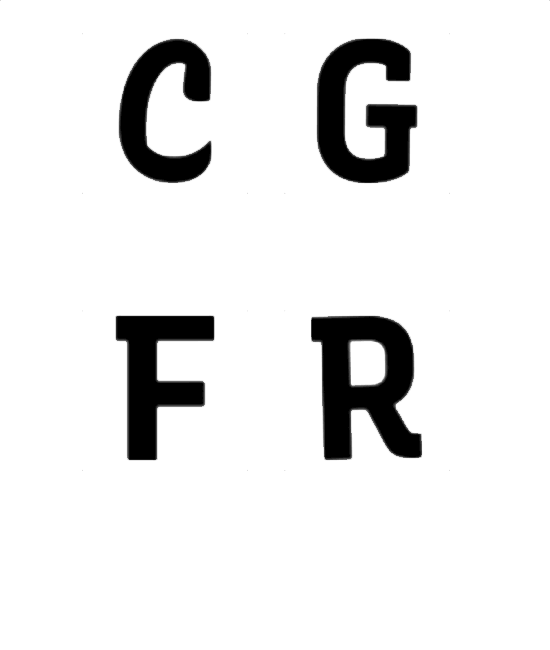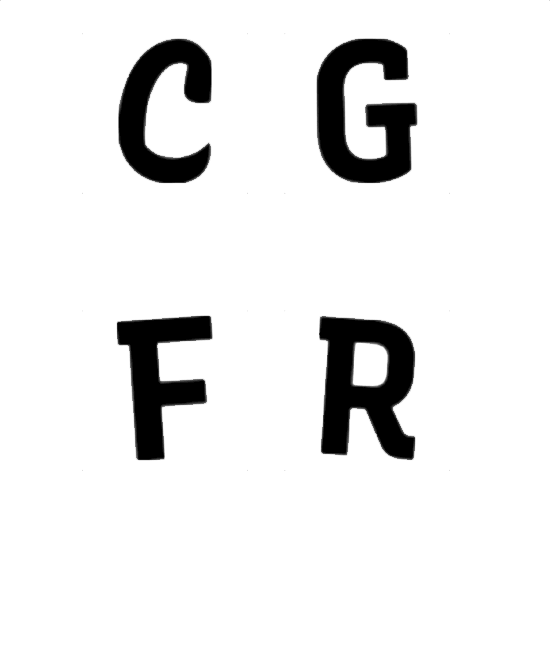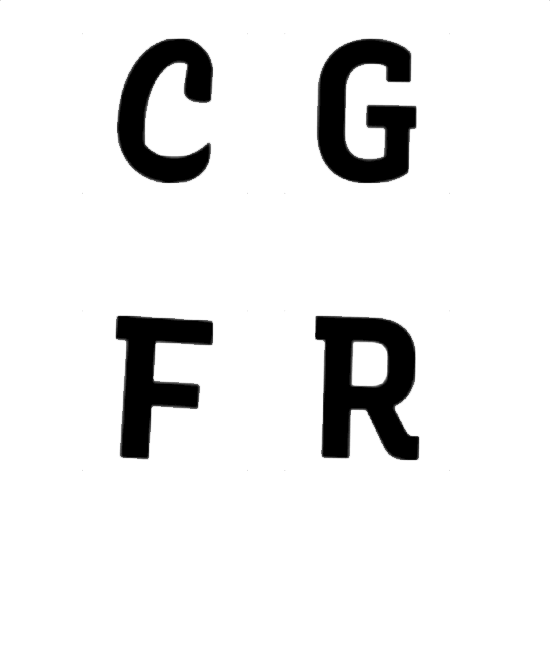
Encoded
Variable fonts store invisible data in the form of values that control how each letter renders across one or more axes. This project weaponizes that latent information to embed encrypted messages inside ordinary text, even in print.
A poster advertising a community garden. A flyer for a lost cat. To the human eye: mundane. To someone with the decoder: coordinates for a safe house, legal resources, emergency contacts.
Developed as part of my masters thesis at NYU ITP/IMA, with research conducted at NYU Shanghai, Berlin, and New York.
I - The Provocation
II - Process
III - How It Works
IV - At Present
The Provocation
AI has ushered in an era of unprecedented panopticon surveillance. The same technology can enable resistance.
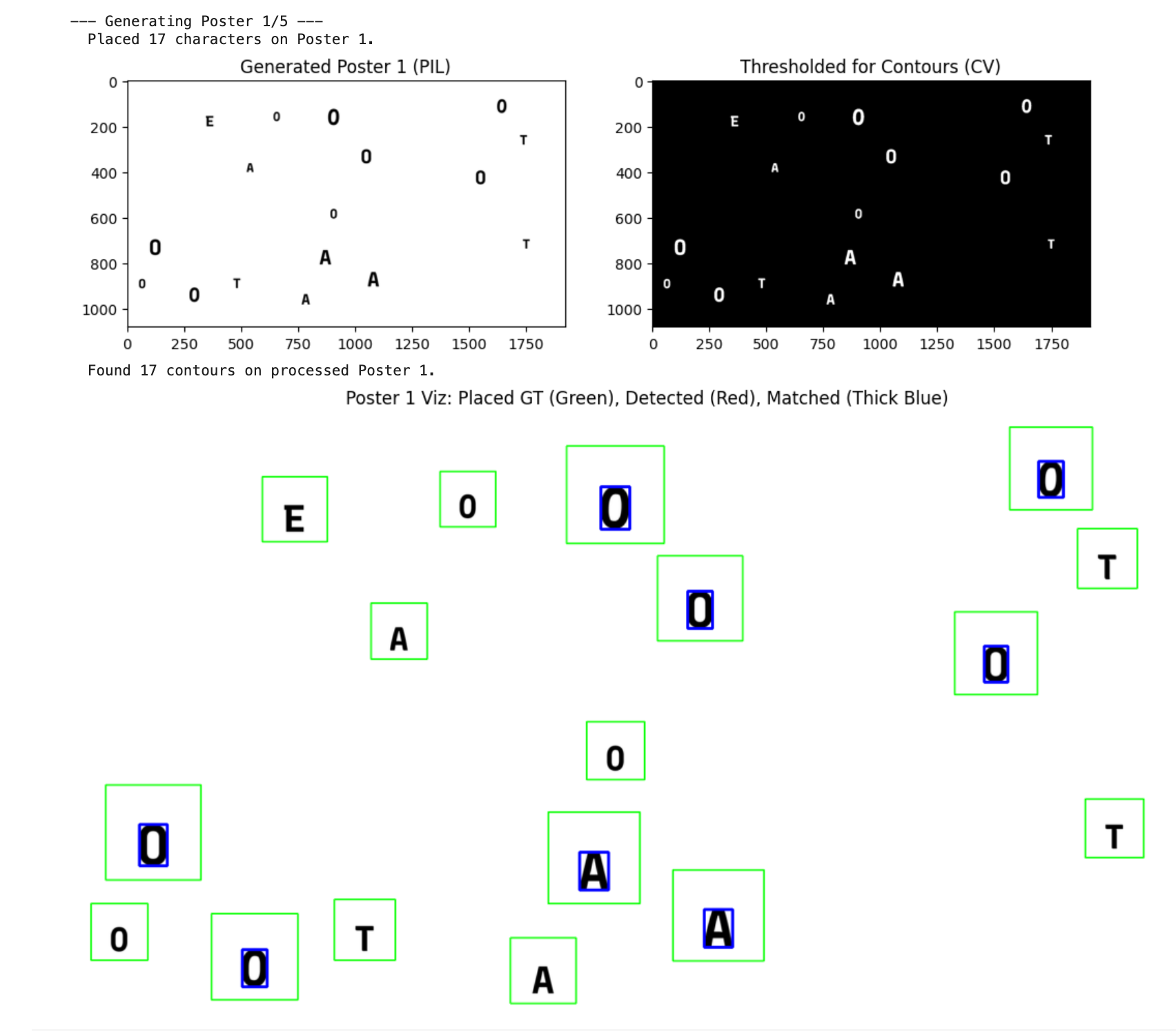
I trained a computer vision equipped machine learning model to detect variations in letterforms imperceptible to humans—tiny shifts along a font's axis spectrum that encode binary data. Each character carries 2 bits. A single sentence carries a hidden payload.

Process
Phase 1: Message Encryption Tool
The tool contains everything to conceal a message and is operable entirely offline allowing users to truly obfuscate their actions.
Phase 2: Distribution of Encrypted Glyph
By allowing dissemination to take place offline, obfuscation of the in-group members and the security of its message is ensured.
By allowing dissemination to take place offline, obfuscation of the in-group members and the security of its message is ensured.
Phase 3: Discovery
The in-group knows what to look for. A photograph captures the payload, initiating the decryption sequence.
The in-group knows what to look for. A photograph captures the payload, initiating the decryption sequence.
Phase 4: Decryption
The model reads the axis variations and reconstructs the hidden message. 128-bit encryption ensures only those with the key can unlock it.
The model reads the axis variations and reconstructs the hidden message. 128-bit encryption ensures only those with the key can unlock it.
How it works
Encode → The sender inputs a cover message and a secret message. The tool renders each letter with precise axis variations that encode the hidden data, outputs a portable SVG.
Distribute → The encoded text lives on posters, flyers, signage—physical media in public space. No digital trail. No interception point.
Decode → The recipient photographs the text. The model reads the axis variations, reconstructs the hidden message. 128-bit encryption ensures only those with the key can unlock it.
The In-Group Signal → The system requires priming. The sender tells their network: "look for posters mentioning a full moon." This shared knowledge is the first lock. The encryption key is the second. Without both, the message is invisible—even if you know the system exists.
At Present
With the ever-changing landscape of machine learning and computer vision, I'm continuing to develop and refine the accuracy of the tool.